Updated on June 21, 2023, by OpenEDR
This article will cover the fundamentals of EDR in cyber security, including what it is, how it functions, the benefits and challenges it presents, and suggestions for using it in your organization. Get comfortable because you’re about to discover the many benefits of EDR.
What is EDR in Cybersecurity (Endpoint Detection and Response)?
Sophisticated assaults on endpoints like PCs, smartphones, and servers can be thwarted with the use of endpoint detection and response (EDR) technologies. The fundamental objective of EDR is to facilitate the monitoring of business equipment in real time, hence facilitating the detection of malicious activity.
Unlike traditional antivirus software, which relies on signature-based detection to identify known malware, EDR uses more sophisticated methods, such as behavioral analysis, to detect new and undiscovered threats. That’s significant because it could stop attacks that other protections have missed.
Also, the EDR tools‘ investigation and remediation features allow security teams to react quickly to attacks. With these preventative measures in place, firms can respond rapidly to cyber assaults and mitigate their effects.
Today’s cybersecurity strategies are useless without understanding what is EDR in cybersecurity. By providing cutting-edge endpoint monitoring and powerful threat identification and response tools, EDR helps businesses stay one step ahead of today’s constantly shifting threat landscape.
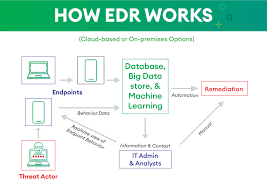
How EDR Works – Endpoint Cyber Security
Now that you know what is EDR in cybersecurity, let’s see how it works. Cybersecurity solutions like endpoint detection and response (EDR) can help businesses spot and counteract online threats as they unfold in real time. Endpoint detection and response (EDR) software keeps an eye out for irregular behaviour on computers, servers, and other network nodes.
When an endpoint acts unexpectedly, the EDR software will send out notifications with specifics about the incident. Because of the warnings, security professionals can swiftly look into the matter and decide whether or not it represents a real threat.
Signature-based detection, behavioural analysis, machine learning algorithms, and heuristics are just some of the approaches EDR uses to identify potential risks. The behavioural analysis tracks how apps perform on endpoints over time, while signature-based detection uses predefined signatures to identify known malware.
Machine learning algorithms employ past data to construct normative user behaviour models, which are then used to evaluate new or unusual conduct. File attributes, such as code complexity and source information, are analyzed by heuristics to detect malicious software.
Automatic remedial procedures, such as isolating affected machines or terminating malicious activities, can be carried out by EDR solutions once real threats have been recognized.
With its superior real-time replies and cutting-edge technological stack, endpoint detection and response offer substantial advantages over conventional antivirus solutions.
The Benefits of EDR
With the knowledge of what is EDR in cybersecurity, you can begin to use it because having an endpoint detection and response (EDR) system in place is now crucial for any business’s cyber defences. There are many ways in which EDR helps businesses safeguard their endpoints from cybercrime.
The speed with which security events can be identified and dealt with in real time is a major benefit of EDR. EDR solutions with extensive analytics capabilities can detect irregularities in user behaviour or network traffic and immediately react by alerting administrators or isolating affected devices.
The use of an EDR solution also provides full visibility into the endpoint infrastructure. All file transfers made on any networked device can be monitored, allowing you to identify the origin of any security holes.
Additionally, most contemporary EDR technologies feature improved threat-hunting capabilities, which improves your readiness for proactive threat management. Without using previously identified attack signatures, machine learning methods allow for the detection of hitherto unseen threats.
By accelerating incident reaction times, increasing network visibility, and facilitating proactive threat intelligence collecting, EDR offers numerous advantages over conventional security solutions.
What are the critical components of EDR in cyber security?
EDR for cyber security provides organizations with a way to collect, analyze, and organize data connected to the endpoints. There are specific components involved in the EDR. Here are these explained:
- Detection
It is one of the standard components of EDR solutions. With the help of this solution, analysts can detect the primary cause of cyber threats and consider taking steps to mitigate the threats.
- Containment
The EDR solution detects malicious files and contains them. A malicious file can infect many applications, processes, and users.
- Investigation
Once the threat has been detected and contained, the EDR investigates the nature of the threat. The problem can be there, which must be investigated promptly to avoid further damage.
- Elimination
It means the culmination of the previous steps- detection, containment, and investigation. EDR provides critical knowledge about the threat. The elimination process depends on gathering essential information about the danger.
The Challenges of EDR in Cyber Security
Just knowing what is EDR in cybersecurity isn’t enough. Implementing endpoint detection and response (EDR) in your organization can be challenging challenging. One of the main challenges associated with EDR is the vast amount of data that needs to be analysed in real time. Since EDR solutions collect data from various endpoints, it’s essential to have proper storage and processing capabilities.
Additionally, managing multiple endpoints across different platforms and operating systems can pose a significant challenge for organizations lacking the expertise or tools required for successful implementation.
Despite these challenges, implementing an efficient endpoint detection and response system remains crucial for organisations looking to strengthen their cybersecurity posture amidst growing cyber threats.
Conclusion – What is EDR in cybersecurity
An integral part of any effective cybersecurity strategy starts by knowing what is EDR in cybersecurity and utilising it for your work. It facilitates the rapid identification, investigation, and resolution of security incidents within businesses. EDR solutions can help prevent security breaches from spreading by keeping tabs on endpoints in real-time. Continuously improving an organization’s cybersecurity posture necessitates the use of endpoint detection and response (EDR) technology. To remain ahead of today’s cyber risks, businesses of all sizes now need EDR because of its ability to monitor endpoints in real time, identify possible threats preemptively, and automate incident responses. The time to implement an EDR solution is now if you haven’t already.