EDR System:
Endpoint detection and response (EDR) is a comprehensive endpoint security system that includes real-time continuous tracking/recording and data collecting with auto-run reaction and analysis capabilities. It is also well-regarded as an endpoint threat detection & response (ETDR)
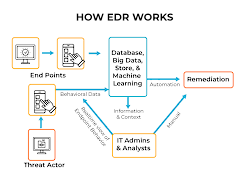
Security EDR Performance
Anton Chuvakin of EDR Gartner proposed this term to talk about emerging security systems that can identify and analyze malicious activity on hosts and endpoints, depending almost entirely on automation to help security teams recognize and react to attacks quickly.
An EDR security system’s essential functions to determine when to use EDR are as follows:
- Monitor and gather endpoint activity data that could signal a vulnerability.
- Examine this data for threat patterns.
- Respond to recognized threats automatically to remove or contain them and notify security personnel.
- Tools for forensics and analysis to analyze detected potential threats and look for suspicious behavior
When to use EDR System?- Consideration for an EDR Solution
These are a few key features to look for in an EDR solution to plan when to use EDR:
Incident triaging flow- By automatically triaging suspicious events, an EDR solution can assist in preventing alert fatigue. This allows security professionals to prioritize their investigations better.
Threat hunting- This can help in the proactive detection of threats and prospective intrusions.
Data aggregation and enrichment- Are required to offer context, which assists EDR systems and security teams in distinguishing between false positives and genuine threats.
Integrated response- Allows teams to analyze evidence and respond to security incidents quickly.
Multiple response options- Allow teams and technologies to respond appropriately to an event. Responses, for EDR example, should cover eradication and quarantine abilities.
Endpoint Detection and Response (EDR) Best Practices – How EDR Works
Consider the following best practices to know when to use EDR while implementing EDR in your organization.
Integrate with Other Tools
EDR solutions are aimed at protecting endpoints but cannot offer complete security coverage for your businesses’ digital assets. EDR should be used with other solutions such as patch management, antivirus, firewalls, encryption, and DNS protection as part of your information security strategy.
An EDR security solution must interact with your existing SIEM (Security Information & Event Management) solution. When network-wide faults are found, a SIEM monitors them and sends alarms. SIEM can be used to centralize multiple security operations, including log gathering. Centralization can help you respond to events and evaluate data more quickly.
Use Network Segmentation
When to use EDR while responding to threats, certain EDR systems separate endpoints; nonetheless, they do not replace network segmentation. Some EDR examples are as follows:
A segmented network- A segmented network enables endpoints to be restricted to specific services and data repositories. This can considerably lower the likelihood of data loss and the extent of harm caused by a successful attack.
Ethernet Switch Paths (ESPs)– They can aid in network security. ESPs allow you to conceal the network’s structure, preventing attackers from readily moving between network parts.
Choosing a Provider As Per Your Businesses’ Specific Requirements
The EDR functionality and cost of an EDR solution can vary depending on the manufacturer. Make the time to research multiple providers before selecting an EDR technology that meets your organization’s demands.
Here are some questions to think about while deciding when to use EDR:
- Can the EDR solution integrate your current operating systems (OS) and applications?
- Is the solution compatible with third-party security tools?
Integration is essential for ensuring that your security plan runs properly. Yet, there are other more factors to consider. Prepare your question per your current conditions and needs, then select the relevant tool.
Know that EDR Solutions Need Human Talent
EDR solutions can generate hundreds of thousands of warnings daily when deployed over large networks with many endpoints. To efficiently respond to warnings, you must establish a prioritizing approach that decreases the number of false positives while keeping your team active.
Several methods exist to limit false positives, but you also require security analysts to assess the data produced by the system. You can either engage internal staff or hire external service providers.
Conclusion – When to use EDR System?
Endpoint detection and response, also known as endpoint detection and threat response, is an endpoint security system that continually monitors end-user devices for cyber threats such as ransomware and malware.
EDR solutions capture data regarding endpoint device behavior, such as laptops, servers, and mobile devices. This information is evaluated based on when to use EDR to discover unusual activities and attacks.
EDR security solutions offer users comprehensive protection for better visibility and keep proper control over everything going on at the interface within the production systems and the internet, along with all of the potential risks and malicious behaviors. Open EDR is one of the best EDR solutions available that provide unmatched protection. Contact us to learn more about Open EDR and learn when to use EDR system to improve your company’s security. Visit for more
See Also:
What is XDR
FAQ Section