OpenEDR Blog

Introducing the game-changer in cybersecurity: Endpoint Detection and Response (EDR). As threats become more sophisticated, traditional security measures no longer cut it. That's where EDR technology comes in - a powerful solution that...

In, End Point Detection, The world has opened an endless number of possibilities for people around the world. They are taking their business to another level. But unfortunately, they are always on the borderline of being digitall...

Cybersecurity today is not just limited to prevention. Cyberattacks have become a part of our world. So, enterprises must always be prepared to respond proactively to threat actors. An effective way of responding is through managed EDR...
Endpoint Detection and Response Meaning: EDR has become a buzzword in the sphere of cybersecurity. But what does EDR stand for? It means Endpoint Detection and Response. EDR is a security technology that detects threats throughout your...
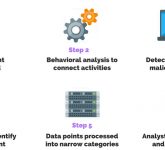
What is an EDR? Are You Worried About Endpoint Security for Your Organization? With cyberattacks becoming ever more sophisticated, having an effective endpoint detection and response (EDR) solution in place has never been more cri...

Protecting digital assets has never been more crucial in an ever-evolving digital environment, where cyber threats continue to evolve in sophistication and severity. When it comes to security, knowing What endpoint detection and re...

Identify and mitigate a threat in cyber security In the interconnected world, there is one thing that continues to evolve, and that's the cybersecurity threat. The landscape of the threats in cybersecurity is rising day by day, le...

Mitigating Insider Threats with Endpoint Detection and Response (EDR) Solutions: Insider threats. Just the phrase itself conjures images of shadowy figures lurking within your organization, ready to create havoc from within. But whi...

A growing number of cyberattacks has led businesses to take stricter measures. The modern business landscape is seeing increasing cybersecurity threats and sophisticated cybercriminals. Because of the number of cyberattacks, multip...

Ensuring the cybersecurity of all endpoints associated with a network, including laptops, mobiles, IoTs, etc., has always been a challenge for companies and organizations. With the evolution and increase in the frequency and severity o...