What is Threat Detection and Response Solutions?
Is your device linked to the internet, or do you use a closed network in the office? If the answer to any of these questions is yes, your device falls into the category of an endpoint. An endpoint refers to a device physically present at the network’s end. They are crucial points for a cybercriminal to gain control of the target network.
An endpoint detection response, or EDR solution, is a cybersecurity technology that identifies and responds to malicious behavior on endpoint devices. These devices can be anything from smartphones to servers and laptops. EDR is a critical tool for IT security teams in this dynamic digital landscape. Let’s find out more about choosing the best EDR for your organization.
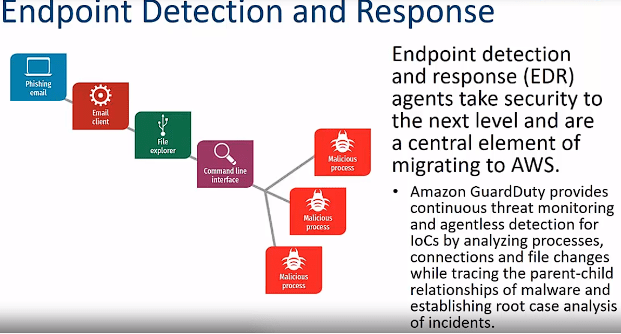
Why Organizations Need Advanced Endpoint Threat Detection and Response
Organizations today are exposed to an array of cyberattacks. From opportunistic attacks to advanced ones, cyberattacks have become pervasive. Although network-based defenses effectively block substantial cyberattacks, malware can bypass the defenses.
An endpoint detection response solution enables a business to enforce more robust security and optimize its chances of detecting and responding to threats. An EDR capability lets you detect, investigate, and rectify sophisticated threats that evade traditional defenses.
An EDR is vital in the defensive security strategy of an organization because of the following:
- The rise of remote work: A growing remote workforce has increased the attack surface because employees connect to business networks from numerous devices. EDR secures these endpoints by providing centralized monitoring. It ensures seamless security across devices.
- Quicker incidence response: Endpoint detection response automates threat containment and reduces the time required to respond to security incidents. Thus, it leads to less business disruption.
- Minimizes dwell time: If attackers remain undetected in a network, the damage they cause dramatically increases. EDR reduces this time (dwell time) by proactively finding and addressing security incidents. This minimizes the dwell time and limits potential damage.
How to Choose the Best Advanced Endpoint Threat Detection and Response Solution
Choosing an EDR that secures your organization’s data in the best possible way is critical. Ask yourself these simple questions to find the right solution.
Does the EDR Capture Threats Crucial for Your Organization?
The EDR you choose should have in-depth abilities to identify and respond to complex threats your usual antivirus products miss. For example, sophisticated attacks like file-less malware present in memory are easily missed by even the most advanced antivirus. However, an efficient Endpoint Threat Detection and Response (ETDR) detects malicious code in memory.
Can the EDR Zero in on Threats That Truly Matter?
Usually, an average endpoint detection response solution detects almost everything suspicious. However, a downside is that they produce a huge volume of alerts, so much so that security analysts find it difficult to keep up with them. So, they modify the solution setting to produce fewer alerts.
Its negative consequence can be seen in the threats being missed by the organization. So, you need to factor in the alert volume that an EDR generates while choosing one. Look out for a solution that only alerts about significant threats.
How Easily Does the EDR Let You Respond to Threats?
A robust endpoint detection response solution guides security personnel to address the threat quickly. An EDR that maps to MITRE ATT&CK framework facilitates effective and quick remediation. It gives a centralized resource that the security personnel can use.
An advanced EDR makes responding to threats seamless. When an alert comes, all that the security staff needs to do is access their EDR dashboard and take the needed actions.
Can the EDR Integrate with Other Tools?
An effective EDR functions as a single aspect of your entire information security strategy. It operates alongside tools like antivirus, firewall, encryption, patch management, and DNS protection. This ability of an EDR tool to integrate makes the daily workflow more efficient and easy. The integration of an EDR with other security tools lets you develop a holistic security ecosystem.
Is the EDR Easy to Setup and Use?
A good endpoint detection response solution is easy to configure and use. You don’t want to spend most of your day learning a complex tool. So, a robust EDR is not only effective but also very easy to understand. It has various options to remediate complex threats and anomalies.
A centralized management console lets you view the security status of every endpoint. You can also set up policies, and investigate, and address various security incidents.
Does the EDR Meet Compliance Requirements?
A robust EDR fulfills all the regulatory and compliance requirements applicable in your place. These include HIPAA or SOC2. The provider of the EDR should have a sound data protection policy. The solution itself should encrypt data and ensure it is transmitted safely.
Final Thoughts – Advanced Endpoint Threat Detection and Response (ETDR) Solutions
Endpoint detection response technology is a significant part of a security strategy. Xcitium’s OpenEDR® is a powerful open-source endpoint detection and response platform that offers analytic detection with MITRE ATT&CK visibility. It covers physical and virtualized environments, letting security teams quickly uncover incidents and take suitable actions to remediate threats. Visit Xcitium today to learn how your organization can leverage the tool to stay protected in today’s digital landscape.
See Also: