Updated on March 2, 2023, by OpenEDR
Need EDR Security Solution for Your Organization
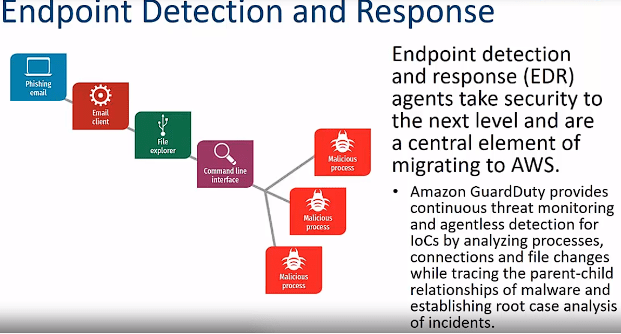
EDR is an Endpoint detection and response system that continuously monitors threat-related information on the endpoints of your business. The purpose of this solution is to detect security breaches and respond to potential threats promptly. Your organization can get real-time visibility into known and unknown threats through EDR solutions. Here is how this system works.
Collecting Data from Endpoints
The very first thing an EDR software does is monitor all the endpoints connected to your network. These days, Open EDR® offers endpoint security to both on-premises and cloud-based devices. Whether you want to protect computers on your business building and remote devices used by your employees, this system can safeguard all endpoints.
It collects all the data from the endpoints, such as communications, processes, user logins, activities, etc., and stores them in a centralized location. Most of the time, this storage location is cloud-based, so your IT team can easily access it from anywhere in the world.
However, you can also get on-location and hybrid cloud options based on your organization’s needs and requirements. Analyzing The Data This solution employs machine learning, endpoint behavior analysis, and Artificial intelligence tools to analyze this data. It also uses signature-based detection technology like the one you get on an antivirus. When it finds any suspicious file, it compares the code with the existing malware database.
If a code matches the existing database, the system will contain the threat. For example, when you go with an Open EDR® solution, it will bring a threat intelligence feature, which can offer you the context of a threat. You can easily detect attacks on your system by comparing network and endpoint activities. Flagging and Responding to Malicious Activities As an EDR Security identifies the threat, it flags the suspicious activities and sends a security alert to IT Administrators. The best part of this solution is that it responds to threats automatically.
Sometimes, security personnel is not available to respond to a threat. In that scenario, this software performs much-needed tasks. For example, it isolates an infected endpoint temporarily so malware won’t spread in your network. This isolation prevents the network-wide attack. Retaining Data for Future Use When you invest in the most reliable and effective EDR Solutions, such as Open EDR®, you can make the most of its proactive threat-hunting and Forensics tools. If you want to secure your organization, performing a deep analysis of an incident is essential.
If malware affects your endpoint, you need to understand how this attack happened and what endpoint was vulnerable. In the presence of this tool, you won’t need to perform any vulnerability assessment, as you will be able to know where the problem lies. It’s easy to tighten your system’s loose security ends via this software.
Why is EDR Security the Need of the Hour?
Sophos’s “The State of Ransomware 2022” report states that 78% of organizations encountered ransomware attacks in 2020. The FBI’s Internet Crime Complaint Center had 3,729 complaints about ransomware attacks in 2021.
The fact is that cybercriminals are using sophisticated malware, ransomware, Trojans, etc. They no longer use file-based malware but also try more advanced file-less attacks. Many attackers use advanced persistent threats APT techniques -where they remain present in your system and keep exporting your organization’s confidential data while staying in the blind spot.
You can block several attacks through a network-based defense system, but some malware carried by removable media still bypasses them. So, investing in the most advanced EDR security tool is essential.
Cybercriminals EDR Security solution
It is needed more than ever as more organizations have moved to remote working. Employees working from home use many devices to connect with your system. They could be more vigilant about security updates and patches. Cybercriminals know that thereby remote devices are easy targets for them. If you want to prevent attacks from remote devices, you need to keep an eye on all these remote devices, and it’s where the EDR solution fits the picture.
When you have this system, it will continuously monitor all connected endpoints. Your security team can check on-site and remote devices from one single dashboard.
Wrap up – EDR Security
You can prevent known and unknown threats through an advanced EDR Security tool. A data breach costs millions, and you can avoid it simply by securing your endpoints through this software.
With this system’s presence, your security team can proactively hunt for threats, and they won’t need to spend weeks in attack analysis and prevention. You can avoid financial loss and improve productivity through endpoint security software, so always try to invest in it.
See Also What is XDR How To Deploy EDR Endpoint Detection and Response